Personal Security in Social Media
Keep yourself safe in real life by being aware of what you are posting on social media.
Continue reading
Group Security in Social Media
Keep your friends safe in the age of social networking.
We have all seen the 'wall of crazy' on various shows and memes. Especially where someone is mapping out the connections between individuals and events to uncover "the truth." And as crazy as the lines and miles of string may seem, it is not actually that far off.
We have discussed in a previous article about how individuals can be profiled based on social media data, and how that profiling process includes interactions between individuals that they are connected to. This is part of the foundation of mapping out a social network.
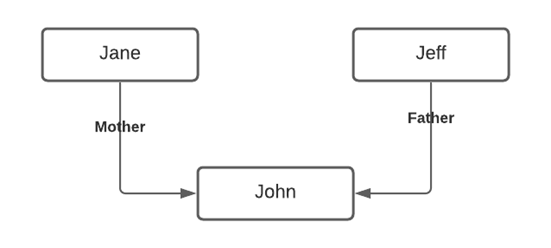
Let us begin by understanding that we can, and generally are, part of multiple networks. The first part of mapping an individual's network starts with the family. For this exercise we will continue with John from the previous article. We know John was born to Jane and Jeff. We can visualize Jeff, Jane, and John, and the relationship between them.
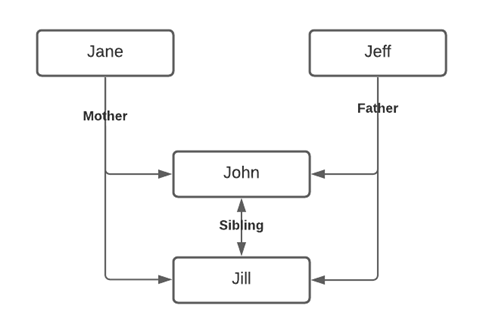
Now that we have established the connection for parentage, let’s evaluate siblings. At first, this may seem easy to accomplish. Jeff and Jane had another child, Jill, which establishes the relationship between them as sibling.
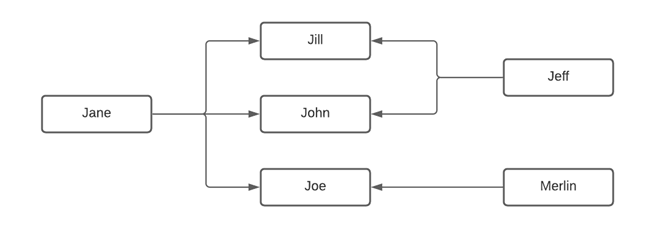
But what do you do if, for some reason, something happened to Jeff, and Jane has another child from a different relationship? What does that type of map look like? It depends on which relationships you are mapping. For example, if you are mapping the parentage for all siblings it would look similar to this:
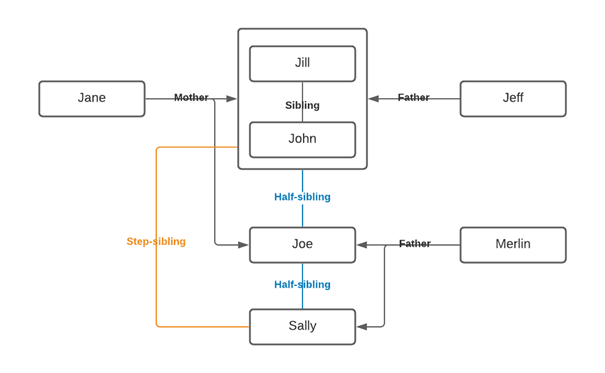
However, if you are more interested in their relationships, consider the following. Merlin had another child before Joe, so we are mapping the relationship between the 4 individuals. The mapping suddenly becomes slightly more difficult, but we can manage by grouping the related entities.
So now that we’ve established his immediate family’s map, we can begin mapping John’s friends and colleagues. To begin, we look at all the people that he’s connected to on each channel. Let’s assume for this exercise that he only participates in 2 channels to keep things simple: a personal network and a professional network.
Let’s compare the first couple of friends on John’s list: William and Jessica. We can see that there is a ‘friend’ relationship between them, but we have yet to determine the extent of the relationship. And we can also see that John is a ‘mutual friend’ that links the two. Many social networking services will use this type of data to make suggestions to users to further build out their network or to identify contacts that they know as part of the service’s experience.
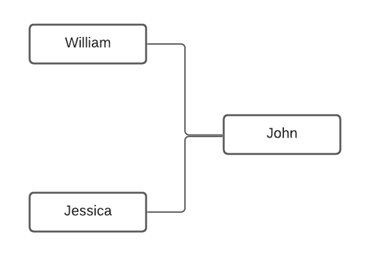
Now, if we look at both John and William’s employment information from their personal social profiles, we can see that they have also worked together. So, if we look at their professional profiles and begin to build out a further map and see that William and Jessica are connected professionally, but not personally.
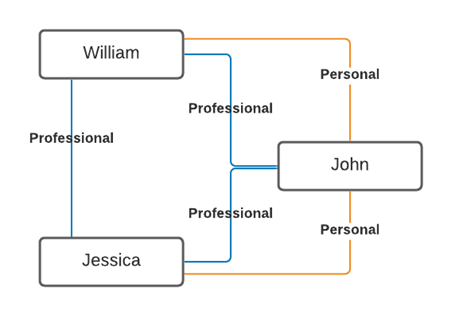
As we begin to look deeper into the interactions between William and John, and between Jessica and John, we see many positive interactions between the 2 pairs. However, we see that John and William attend many events together instead of simply interacting online. Jessica and John, by comparison, do not attend any events together. This shows that the relationship between John and William seems to be stronger.
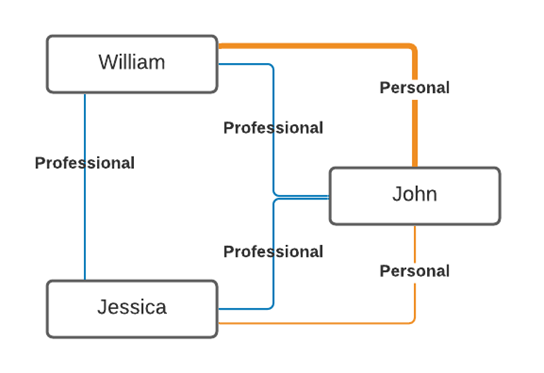
Even further review between the 3 individuals interactions shows that there are some comments on some posts where John was a common link between Jessica and William that are decidedly not friendly. They have strongly differing opinions. And while John’s views and tone keeps him in positive terms with Jessica, her interactions with William are of enough difference that Jessica and William have decided to keep themselves to a strictly professional connection (even though they frequently debate each other’s posts in the personal network service). Now that we have established how they are connected and the tenor of their relationships our map begins to look a little more complete.
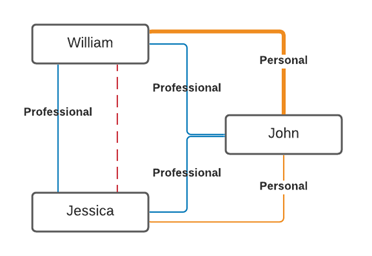
So, what does social network mapping have to do with OPSEC? We have only talked about a couple of types of social networks. Remember, OPSEC is about using the small, seemingly insignificant pieces of information to reveal a larger picture. For example, in 2018 a security breach was identified by a student that came across the fitness tracking site Strava.com. Using the site he was able to identify areas of fitness activity (such as hiking) with frequency in areas that there should not have been hikers or established trails. As it turned out, these were patrol routes and military bases where people were wearing devices that could track where they were and patterns began to emerge.
To show how this is applicable, I know of an area that has some trails. From a typical satellite view it doesn’t look like there is any traffic in the area.

However, when you apply a heatmap from the various hikers that have worn a fitness device while walking that area you can see multiple trails as well as the areas where there does not appear to be any traffic.

Now, while this information opens many possibilities for hunting, hiking, and camping in more secluded areas, this type of data is something to keep in mind. The best way to avoid inadvertently submitting this type of data is to leave all geo-capable devices including cellphone and exercise tracking devices at home. Also, if you are practicing survival techniques, you might want to consider limiting what you share. Pictures of local flora and fauna can be used to help determine your position. Multiple posts from people within your network around the same time can indicate a group of friends that are training together. And, returning to personal security concepts, if a group is identified as taking frequent trips together for extended periods of time it can create opportunities for malicious actors to take an action against one of the members in your group if someone posts just the right piece of information that indicates when, how far, and how long someone will be away from their home.
So be safe. Both individually and as a group, be mindful as to what you are posting. A picture of an individual is powerful, but a picture of a group of individuals can be even more so.